Hello,
I am having network problems with NVR-108MH-D-8P.
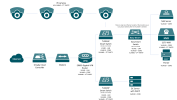
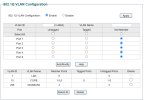
I have recently reconfigured our network to include multiple VLANs and reconfigured DHCP servers. The NVR used to be on the 192.168.1.x subnet and the IP address I set was static to 192.168.1.40. Now as I am planning to have the NVR set onto a new VLAN interface which is called 'Core Network' under VLAN10 and have it to reserve the IP address from the DHCP server as 192.168.10.30. The Core Network VLAN is controlled by a DHCP on a DC controller rather than the router (which is TP-LINK ER605).
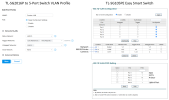
Currently the NVR is connected to a 5-Port unmanaged switch (I may have to consider changing this to a smart switch if this is the case) along with my NAS and printer, both of these devices are also connected to the same VLAN which is controlled by TP-LINK Omada and it is connected from a single port on TP-LINK TL-SG2016P smart switch.
When I went to change the network settings on my NVR to DHCP, it randonmly gives an IP address with 192.168.1.168 which to me looked incorrect, particularly with the NVR being on VLAN10. I could not connect to this IP address as the automatic configuration also gives the gateway as 1.0.0.0 which is unusual. So I thought of looking at setting static on the NVR to the IP configuration I wanted it to be and then it picked the NVR through the network but does not show the IP address I set it to, which to me is very frustating.
I've looked at the IPv4 setting in Expert mode and changed this, but comes back with the conflicting IP warning. It seems this only works with two default IP addresses I believe which they are: 192.168.254.1 and 192.168.253.1
So either this appears to be an issue with the NVR firmware or it is my network configuration.
Please could you give me some assistance on this, it would be greatly appreicated.
Many thanks,
Ben
I am having network problems with NVR-108MH-D-8P.
I have recently reconfigured our network to include multiple VLANs and reconfigured DHCP servers. The NVR used to be on the 192.168.1.x subnet and the IP address I set was static to 192.168.1.40. Now as I am planning to have the NVR set onto a new VLAN interface which is called 'Core Network' under VLAN10 and have it to reserve the IP address from the DHCP server as 192.168.10.30. The Core Network VLAN is controlled by a DHCP on a DC controller rather than the router (which is TP-LINK ER605).
Currently the NVR is connected to a 5-Port unmanaged switch (I may have to consider changing this to a smart switch if this is the case) along with my NAS and printer, both of these devices are also connected to the same VLAN which is controlled by TP-LINK Omada and it is connected from a single port on TP-LINK TL-SG2016P smart switch.
When I went to change the network settings on my NVR to DHCP, it randonmly gives an IP address with 192.168.1.168 which to me looked incorrect, particularly with the NVR being on VLAN10. I could not connect to this IP address as the automatic configuration also gives the gateway as 1.0.0.0 which is unusual. So I thought of looking at setting static on the NVR to the IP configuration I wanted it to be and then it picked the NVR through the network but does not show the IP address I set it to, which to me is very frustating.
I've looked at the IPv4 setting in Expert mode and changed this, but comes back with the conflicting IP warning. It seems this only works with two default IP addresses I believe which they are: 192.168.254.1 and 192.168.253.1
So either this appears to be an issue with the NVR firmware or it is my network configuration.
Please could you give me some assistance on this, it would be greatly appreicated.
Many thanks,
Ben